Three automated ship-to-shore cranes grind to a halt after unusual container movements are detected on the platform below. One thing quickly becomes clear: this is not a mechanical failure—it’s a cyberattack.
This vivid—though fictional—scenario launched a high-stakes training exercise for the U.S. Coast Guard’s 2013 Cyber Protection Team (CPT) last month at Pacific Northwest National Laboratory (PNNL) in Richland, Washington. As cyber threats to the Marine Transportation System (MTS) grow more advanced, exercises like this are helping prepare the Coast Guard’s cyber defenders for the realities of today’s threat landscape.
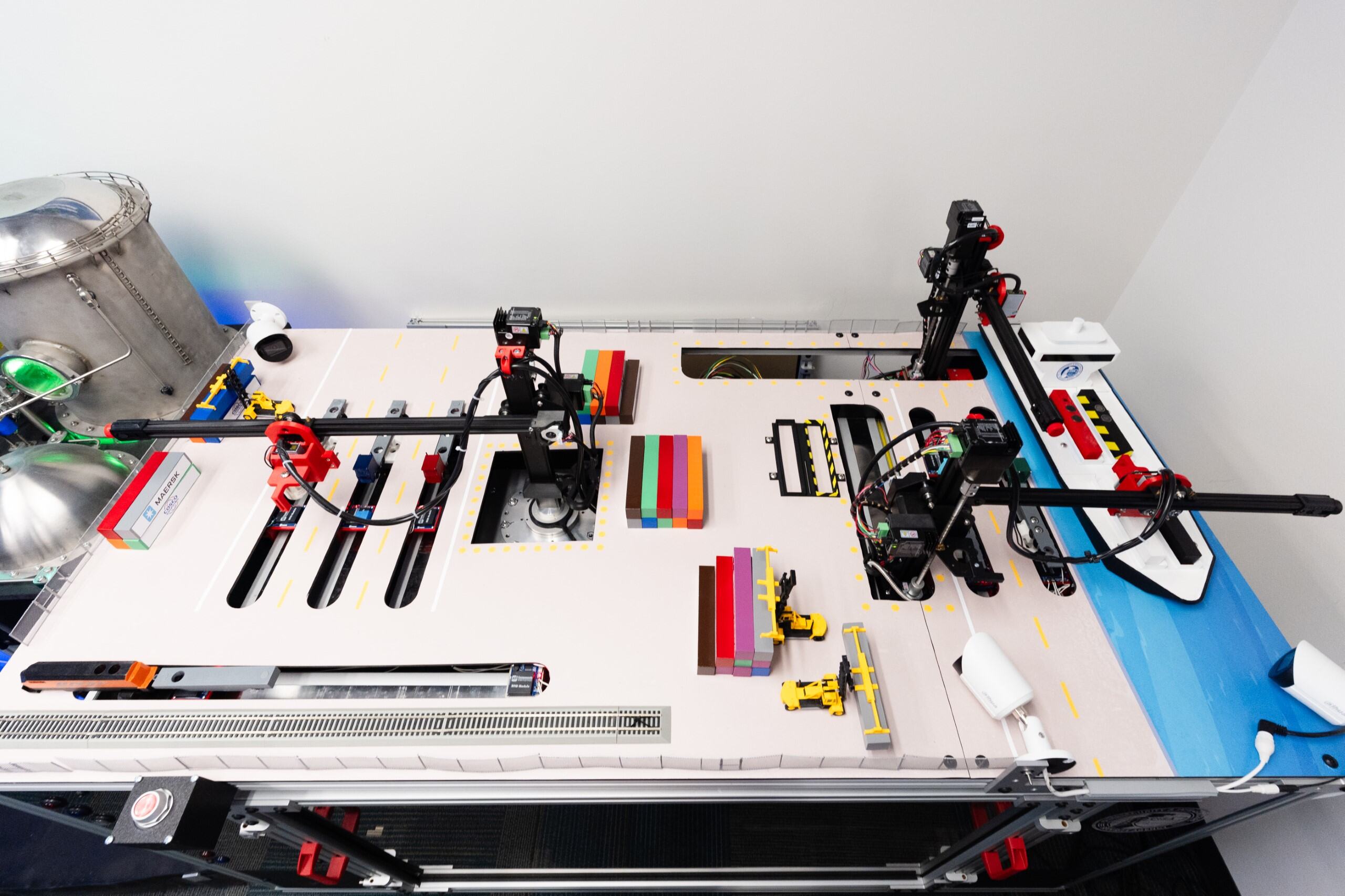
Over the past two years, the CPTs have prioritized developing the capability to detect malicious cyber activity on port technology, including Chinese manufactured cranes. This exercise used the new maritime platform to immerse CPT members in a lifelike simulation of a multi-stage cyberattack on a U.S. container terminal. One of five critical infrastructure platforms located at PNNL as part of the Control Environment Laboratory Resource (CELR) developed and operated by the Cybersecurity and Infrastructure Security Agency (CISA) and PNNL, the maritime platform is the federal government’s most advanced maritime cyber training platform, replicating the Operational Technology and Industrial Control Systems (ICS) found at real U.S. ports.
“This realism is what makes the platform so valuable,” said Donny Mendoza, Deputy Program Manager for CISA projects at PNNL. “It took over a year to build, with the design and fabrication informed by visiting actual seaport facilities to replicate their systems and architecture.”
The simulated attack featured a PNNL Red Team of cyber experts acting as adversaries, breaching networks, establishing persistence, and disrupting port operations—all while CPT members worked to detect, contain, and respond in real time. The scenario forced the team to respond under pressure, identifying how attackers gained access to the Terminal Operating System and developing mitigation strategies for fictional port authority staff.
“Our goal was to replicate not just the infrastructure, but also the stress and operational impact of a real-world incident,” said Alex Reniers, CISA’s ICS Section Chief.

“It’s a live-fire drill in a safe environment,” said Ensign Harold Scott, the team’s Mission Element Lead. “We’re seeing how threat actors move, how effectively we can react, and what actions we can take to minimize operational disruptions.”
For the 2013 CPT, the experience reinforced the critical importance of hands-on training that reflects real-world maritime operations to be ready to respond to future cyber incidents at U.S. ports. As the lead federal agency responsible for protecting and securing critical infrastructure in the MTS, the Coast Guard must remain ready and relevant to face evolving cyber threats. To that end, the maritime platform proved an invaluable tool, noted Chief David Kinnamont, crew lead for the participating team.
“The maritime platform delivered exactly what we needed,” he said, “It was a realistic scenario that improved team performance and sharpened our cyber response skills.”
-USCG-
Resources:
In the news: